12BET – NHÀ CÁI 12BET – LINK VÀO 12BET: ĐĂNG KÝ +100%
Mặc dù mới đi vào hoạt động gần đây nhưng Nhà cái 12BET mang đến cho anh em cá cược nhiều điều mới lạ, hấp dẫn cùng chất lượng dịch vụ trên cả tuyệt vời.
Nhà cái này nổi tiếng với tỷ lệ ăn thưởng cao, chính sách chăm sóc khách hàng tốt cùng kho tàn game khủng nhất thế giới. Cùng tìm hiểu kỹ hơn về nhà cái thông qua những chia sẻ trong bài viết dưới đây.
Giới thiệu về nhà cái 12BET
Hiện nay có rất nhiều anh em đã chọn và tin tưởng nhà cái 12BET làm sân chơi kèo cược bởi nhà cái được xem là địa chỉ chơi game uy tín hàng đầu Việt Nam. Một vài thông tin tổng quan dưới đây sẽ giúp bạn hiểu rõ được phần nào về 12BET.
Nhà cái 12BET đồng thời cũng là nơi phát trực tiếp tốt và hiện đại nhất cho các bộ môn thể thao như: bóng đá, bóng bàn, bóng chày… Chuyên cup cấp một số loại hình xổ số và nhiều loại truyền hình khác nhau.
Cũng giống như nhiều nhà cái ở thời điểm hiện tại nhà cái 12BET luôn tạo ra nhiều điều mới mẽ và hàng ngàn sự kiện và trên hàng trăm trận đấu trực tiếp được diễn ra trong nhiều bộ môn thể thao khác nhau.

Nếu sợ vì sự hạn chế kèo thì 12BET đã làm được điều này để phục vụ nhu cầu của mọi người. Kèo cược ở nhà cái 12BET nhanh chóng và dễ dàng nên đã tạo nên nguồn cảm hứng thú vị và trải nghiệm tuyệt vời cho nhiều anh em mới bắt đầu lẫn những người có kinh nghiệm.
Theo đó, nhà cái 12BET đầu tư, phát triển đầy đủ loại hình đặt cược với luật chơi dễ hiểu, dễ thắng. Từ đó, giúp người chơi có được những trải nghiệm trên cả tuyệt vời, đặc biệt là nhanh chóng kiếm thật nhiều tiền.
Sự mới mẻ của 12BET Club
nha cai 12BET không chỉ nhận được đánh giá tốt từ phía người chơi mà còn cả những chuyên gia lâu năm trong làng cá cược, game trực tuyến.
Nhắc đến 12BET là nhiều người sẽ nghĩ đến ngay một nhà cái có quy một hoạt động lớn, chính sách cá cược đa dạng, minh bạch, rõ ràng,..
Trong nhiều năm qua, 12BET đã không ngừng phát triển và mở rộng quy mô hoạt động ra nhiều nước khác nhau trên thế giới như Lào, Thái Lan, Philippines,…
Mang đến sự tiện lợi tối đa cho anh em cá cược, bởi bạn ở bất kỳ nơi nào cũng có thể trải nghiệm game tại nha cai 12BET một cách dễ dàng.
12BET là một trong những nhà cái thường xuyên áp dụng công nghệ game mới, đỉnh cao mang đến cho người chơi nhiều trải nghiệm mới lạ, chân thực nhất.
Anh em trải nghiệm game tại nhà cái 12BET club sẽ không có cảm giác nhàm chán bởi kho tàn game khủng được cập nhật thường xuyên mỗi ngày.
Điểm mạnh của 12BET
Điểm mạnh nhất của nhà cái 12BET so với những nhà cái tại Việt Nam hiện nay đó chính là tính hợp pháp và Được cấp Giấy phép bởi công ty giải trí và trò chơi tại Philippines (PAGCOR). nhà cái 12BET có thời gian hoạt động cũng khá lâu đời nhưng vẫn giữ vững vị trị như ngày hôm nay là nhờ vào sự tin tưởng và đồng hành của anh em.
Nhằm mang lại những dịch vụ tốt nhất, sự minh bạch, rõ ràng và giúp anh em thoải mái cá cược, nhà cái 12BET club đã ký kết với nhiều đối tác lớn, có tiếng nói trong nền công nghiệp kèo cược. Evolution gaming chính là một điển hình trong sự hợp tác này.
12BET luôn lấy sự uy tín lên hàng đầu làm phương châm kinh doanh và bảo vệ đầy đủ quyền lợi của người chơi.
Nhà cái đến từ SINGAPORE được phát triển bởi Play Tech – một công ty được thành lập từ năm 1999, có bề dày kinh nghiệm trong việc kinh doanh lĩnh vực Casino.
Nhà cái Mu88
Dù chỉ mới xuất hiện ở thị trường Việt Nam nhưng 12BET đã và đang tạo nên những khác biệt đậm nét trong trong thị trường cá cược online.
Trải nghiệm khác biệt tại nhà cái 12BET club
Không phải tự nhiên mà 12BET được người chơi đánh giá là nhà cái uy tín hàng đầu thế giới. Bởi khi trải nghiệm game tại đây bạn sẽ nhận được nhiều tiện ích dịch vụ như sau:
Giao diện website thiết kế khoa học
Giao diện game tại nhà cái 12BET được thiết kế rất ấn tượng. Màu sắc nổi bật, thanh menu sắp xếp khoa học giúp anh em dễ dàng tìm thấy tựa game yêu thích chỉ trong ít phút.
Bên cạnh đó hệ thống âm thanh game chân thực, sống động mang đến cho bạn cảm giác thích thú khi trải nghiệm game.
Đa dạng tỷ lệ kèo
Đến với nhà cái 12BET bạn không chỉ được trải nghiệm kho tàn game khủng mà tại đây còn có đa dạng tỷ lệ kèo. Từ đó giúp bạn thỏa sức lựa chọn kèo cược là thế mạnh của bản thân.
Thông tin khách hàng được bảo mật tuyệt đối
Người chơi khi tham gia game tại nhà cái 12BET biz sẽ yên tâm rằng tài khoản, thông tin cá nhân không bị lộ ra ngoài. Bởi 12BET đã cài đặt hệ thống bảo mật thông tin người dùng nhiều lớp, công nghệ được thiết lập bởi công ty hàng đầu thế giới.
Đặc biệt tài khoản game của bạn tại 12BET sẽ được bảo mật tuyệt đối và không bao giờ xảy ra tình trạng bị hack tài khoản.
Hệ thống chăm sóc khách hàng chuyên nghiệp
Tại 12BET sở hữu đội ngũ nhân viên chăm sóc khách hàng chuyên nghiệp, tận tâm, sẵn sàng hỗ trợ bạn mọi lúc mọi nơi.
Bất kể những ngày lễ, cuối tuần đều có nhân viên của 12BET biz trực. Mỗi khi bạn có thắc mắc cứ liên hệ với 12BET biz sẽ được giải quyết nhanh chóng.
Theo đó người chơi có thể liên hệ với 12BET bằng các hình thức như: Gọi điện thoại trực tiếp, Zalo, Gửi email, live chat,…
Khuyến mãi nổi bật của 12BET
Khuyến mãi tại nhà cái 12BET là điều mà nhiều nhà cái tạo nên sự hung phấn cho nhiều anh em nha cai 12BET cũng không ngoại lệ việc này.
Và đây cũng chính là cách hữu ích giúp nhà cái có thể giữ chân những người chơi mới lẫn dân cá cược lâu năm.
Đối với 12BET cũng không ngoại lệ, nhà cái thường xuyên tung ra nhiều chương trình khuyến mãi khủng và cực kỳ hấp dẫn mỗi ngày để thu hút lượng lớn người tham gia.
Đặc biệt, với những người lần đầu đăng ký được nhận nhiều phần thưởng sốc. Trong đó, nổi bật nhất phải kể đến đó là các chương trình khuyến mãi:
Với ba khuyến mãi đặc biệt dành riêng cho thành viên tại 12BET
Khuyên mãi tặng 100%
Khuyến mãi 12BET tặng 100% cho người chơi mới nạp tiền lần đầu khi tham gia cá cược các sản phẩm: Thể thao, Thể thao ảo, Keno, Numbers game, Slot nổ hũ với số tiền tối đa lên tới 15.000.000 VNĐ
Đối tượng và nội dung:
- Tối đa tiền thưởng lên đến 15.000.000 VND.
- Dành cho tất cả tài khoản lần nạp đầu tiên tại nha cai 12BET .
- Tiền nạp và tiền khuyến mãi phải trải qua 20 vòng cược trước khi thực hiện rút tiền.
- Trong vòng 30 ngày toàn bộ tiền trong Tài khoản game sẽ bị hủy nếu không đạt đủ số vòng cược.
Khuyên mãi tặng 50%
Khuyến mãi tặng 50% cho người chơi mới nạp tiền lần đầu khi tham gia cá cược các sản phẩm: Thể thao, Thể thao ảo, Keno, Numbers game, Slot nổ hũ với số tiền tối đa lên tới 20.000.000 VNĐ
Đối tượng và nội dung:
- Tối đa tiền thưởng lên đến 20.000.000 VND.
- Dành cho tất cả tài khoản lần nạp đầu tiên tại nha cai 12BET .
- Tiền nạp và tiền khuyến mãi phải trải qua 15 vòng cược trước khi thực hiện rút tiền.
- Trong vòng 30 ngày toàn bộ tiền trong Tài khoản game sẽ bị hủy nếu không đạt đủ số vòng cược.
Khuyến mãi hoàn trả 1,5%
Khuyến mãi hoàn trả 1,5% không giới hạn cho các vé cược: Thể thao, Thể thao ảo, Keno, Numbers game, Slot nổ hũ
Đối tượng và nội dung:
- Hoàn trả 1,5% không giới hạn.
- Tiền khuyến mãi sẽ được cập nhật vào lúc 13h hàng ngày.
- Tiền nạp và tiền khuyến mãi có thể rút tiền ngay.
- Không áp dụng chung với các chương trình Khuyến mãi 50%, 100%.
Các sản phẩm cá cược tại 12BET biz
Thị trường Việt Nam ngày càng phất triển một cách mạnh mẽ và dần ổn định hơn với công nghiệp kèo cược.
Để đáp ứng hết như cầu của người chơi trong và ngoài nước với lượng khách hàng khổng lồ như vậy nhà cái 12BET đã cho ra nhiều sản phẩm cá cược cũng như nhiều mô hình kèo cược khác nhau để phù hợp với mỗi người chơi khác nhau.
Đồng thời, 12BET nhà cái bóng đá uy tín singapore còn hỗ trợ người chơi với một chuyên mục hướng dẫn cá cược cực hữu ích dành cho tân game thủ. bắn cá, game bài,
Cá cược thể thao trực tuyến
Thể thao trực tuyến luôn là điều mà nhiều nhà cái khác nhau đã và đang tập trung đa số nhân lực vào mô hình này. Vì đa số người chơi kèo cược mới bắt đầu hay đã có kinh nghiệm lâu dài thì vẫn chiếm phần lớn là cá cược trực tuyến.
Với sự truy cập khổng lồ như vậy 12BET đã tập trung vào sự ổn định cũng như không bị giật lag để cho người cho có những cảm nhận và tin tức kịp thời một cách nhanh chóng.
Đó cũng là điều hiển nhiên mà 12BET nhà cái bóng đá uy tín singapore được nhiều người chơi và nhiều người ủng hộ đến như vậy.
Cá cược trực tuyến trên 12BET không chỉ hướng để một bộ phần cá thể như cá cược bóng đá mà bên cạnh đó có rất nhiều bộ môn khác nhau mà 12BET nhà cái bóng đá uy tín singapore đều được trực tuyến như: bóng bàn, bóng rỗ, bóng chuyền…
Đặc biệt hơn những bộ một điện tử cũng được phát triển trực tuyến cho những an hem đam mê loại thể thao này.
Casino tại 12BET
Tham gia casino tại 12BET bạn sẽ có rất nhiều điều mới lạ. Tại đây không chỉ có mỗi casino ảo mà còn có cả Casino trực tuyến giúp người chơi có thể kết nối với nhiều người khác nhờ công nghệ live trực tuyến.
Nhiều người chơi với nhiều sở thích khác nhau, người chơi thích nhanh gọn với sòng ảo người thì thích vừa chơi vừa đấu trí cũng như kết nối với nhiều người chơi khác khi tham gia Live Casino. Đúng là một trải nghiệm độc đáo phải không nào.
Với nhiều bộ môn khác nhau tại Casino: Poker, Baccarat, Backjack…đã thu hút được phần lớn người chơi trong và ngoài nước . Mỗi bộ môn đều có ưu điểm và nhược điểm khác nhau mà mỗi người chơi có thể chọn và phát huy hết ưu điểm của mình và mang lại lợi nhuận lớn cho bản thân khi tham gia tại 12BET.
Cá cược thể thao ảo
Thể thao ảo đang là tựa game đang được rất nhiều giới trẻ hưởng ứng và chọn làm sở thích để theo đuổi. Với nhu cầu ngày càng lớn như vậy, 12BET đã chọn thể thao E-sport làm “linh hồn” và phát triển mạnh về hình ảnh, giao diện…
Hiện tại, thế giới thể thao ảo hot nhất ở 12BET phải kể đến là: Dota2, Liên minh huyền thoại, Fifa và nhiều game khác nữa. Tất cả đều là những bộ môn thể thao điện tử vô cùng lành mạnh, phổ biến, đang người chơi tại Việt Nam nói riêng và cả thể giới nói chung yêu thích.
Để tạo ra sân chơi cho phần lớn cộng đồng gamer và những người am hiểu về game thể thao điện tử, 12BET ngoài phát trực tiếp các trận đấu còn đẩy mạnh hình thức kèo cược.
Điều này đã thu hút khá nhiều gamer cũng như những người yêu thích những trò chơi này đến 12BET để thử sức với kèo cược. Việc kèo cược tại nhà cái 12BET sẽ góp phần hạn chế vấn nạn như bán độ xảy ra…
Thể thao điện tử tại 12BET
Thể thao ảo đang là bộ môn đang rất nhiều giới trẻ hưởng ứng và chọn làm sở thích để theo đuổi. Với nhu cầu ngày càng lớn như vậy 12BET đã chọn thể thao E-sport làm một bộ phận cá cược để nhiều anh em lựa chọn. Với nhiều bộ môn thể thao điện tử hot nhất hiện nay như: Dota2, Liên minh huyền thoại, Fifa và còn nhiều bộ môn khác nữa tất cả đều là những bộ môn thể thao điện tử vô cùng nhiều người chơi tại Việt Nam nói riêng và cả thể giới nói chung.
Để tạo ra sân chơi cho phần lớn cộng đồng gamer và những người am hiểu về bộ môn điện tử này. Điều này đã thu hút khá nhiều gamer cũng như những người yêu thích những trò chơi của mình để thử sức với kèo cược. Việc kèo cược trên này sẽ hạn chế được những vấn đề như bán độ, vấn đề về thời tiết cũng như nhiều vấn đề cơ bản khác…Điều này cũng mới lạ đúng không nào!
Trò chơi tại 12BET
Sẽ thật tuyệt vời đối với một số anh em muốn nhanh gọn và đơn giãn thông qua các trò chơi nhanh hay mọi người sau một khoảng thời gian kèo cược căng thẳng trong cá cược trực tuyến hay trực tuyến thể thao gamer người chơi có thể vào đây thử giãn và thử vận may qua các trò chơi nhanh ngắn gọn.
Không chỉ là một vài trò chơi mà 12BET đã cho ra đời nhiều loại trò chơi ngắn khác nhau để đáp ứng nhu cầu giải trí cũng như trãi nghiệm dành cho mọi người thích kèo cược để thử giãn. Với nhiều game nhanh mà anh em hay chọn như:
- Quay số: một trong những trò chơi mà được rất nhiều anh em cộng đồng lựa chọn để thử vận may và đôi khi là thắng lớn trong chính trò chơi này.
- Kenno: Sản phẩm Keno Vietlott có 3 cách chơi đó là cách chơi cơ bản, cách chơi chẳn lẻ và cách chơi lớn nhỏ hứa hẹn sẽ đem đến cho khách hàng những trải nghiệm thú vị hấp dẫn.
- Number game: Trò chơi này còn có tên gọi khác như là xổ số, trò chơi số, trò chơi các số, hay bóng số, hoặc kèo số,…
Và bên cạnh đó 12BET cũng đang cho ra mặt một số trò chơi nhanh hứa hẹn sẽ rất hấp dẫn và mới lạ.
Điểm mạnh của 12BET
Tính hợp pháp
Hoạt động cũng khá lâu đời và được sự tin tưởng của mọi người khi đã tham gia và trãi nghiệm tại 12BET. Bên cạnh với sự minh bạch và tạo nên sự tin tưởng dành cho người chơi 12BET đã hợp tác với nhiều đối tác lớn khá uy tín và có nhiều tiếng nói trong nên công nghiệp kèo cược và Evolution gaming là một điển hình trong sự hợp tác này. 12BET lấy uy tín lên hàng đầu và bảo vệ quyền lợi của người chơi.
Nhà cái đến từ SINGAPORE được phát triển bởi Play Tech – một công ty được thành lập từ năm 1999, có bề dày kinh nghiệm trong việc kinh doanh lĩnh vực Casino. Dù chỉ mới xuất hiện ở thị trường Việt Nam nhưng 12BET đang tạo được những khác biệt trong thị trường cá cược online.
Các chương trình khuyến mãi đa dạng và diễn ra liên tục
Hàng loạt ưu đãi sẽ được 12BET phát hành thêm để đáp ứng được nhu cầu của người chơi. Đồng thời 12BET của tạo ra nhiều phần thưởng đặt biệt và luôn trao cơ hội cho những thành viên của mình tại nhà cái này.
Giúp người chơi có được nhiều khuyến mãi để thêm tỉ lệ cá cược cho bản thân góp một phần không ít để thu về được lợi nhuận cho cá nhân mình. Sắp tới 12BET cũng sẽ ra thêm hàng loạt ưu đãi đặc biệt với nhiều hạn mức khác nhau dành riêng cho thành viên của nhà cái 12BET.
Thủ tuc nạp – rút nhanh chóng
Luôn là một vấn đề mà rất rất nhiều anh em quan tâm khi đến với mọi nhà cái. Có khác nhiều câu hỏi về vấn đề nạp tiền 12BET. Mình sẽ hướng dẫn và nói cho các bạn bằng bố chữ: Đơn giãn – Nhanh chóng đó là những gì mà 12BET đã làm được và đang vận hành nó một cách hoàn mĩ hơn.
Tránh thủ tục rườm rà 12BET chỉ mất từ 3-5 phút cho việc nạp cũng như rút tiền 12BET tại đây. 12BET cũng luôn tạo ra nhiều cách nạp và rút tiền khác nhay để cung cấp cho mỗi người chơi một thao tác khác nhau để họ có thể dễ dàng giao dịch hơn.
Chính sách chăm sóc khách hàng 12BET
12BET được đông đảo anh em đánh giá là nhà cái có chính sách chăm sóc khách hàng khá chu đáo và tận tâm. Kể cả những khách hàng chưa tham gia trải nghiệm game vẫn được 12BET hỗ trợ nhiệt tình.
Phương châm chăm sóc khách hàng 12BET
“Tận tâm, chu đáo, am hiểu” là phương châm chăm sóc khách hàng tại nhà cái 12BET. Bởi 12BET có đội ngũ chăm sóc khách hàng không chỉ giỏi, am hiểu chuyên sâu mà còn rất tận tâm, chuyên nghiệp.
Từ trước đến nay, 12BET chưa nhận được một khiếu nại nào từ phía khách hàng. Vì mỗi khi có thắc mắc nào, người chơi chỉ cần liên hệ với 12BET là sẽ được giải đáp nhanh, hiệu quả nhất.
Trải nghiệm thực tế chăm sóc khách hàng 12BET
Thực thế khi chơi game, anh em có thể liên hệ với 12BET bằng nhiều hình thức khác nhau như: Gọi điện thoại trực tiếp qua số hotline, gửi email, trò chuyện cùng nhân viên bằng Live Chat, tư vấn qua các kênh mạng xã hội như zalo, viber,…
Những nhân viên chăm sóc khách hàng của 12BET trực tuyến 24/24, do đó khi bạn có bất kỳ thắc mắc nào chỉ cần liên hệ sẽ được hỗ trợ nhiệt tình.
Đặc biệt những tay chơi mới vào nghề cần phải nhờ sự hỗ trợ nhiều từ phía nhà cái để nắm rõ thông tin, cách chơi, tư liệu game,…
Đăng ký và đăng nhập tại nhà cái 12BET
Hình thức đăng ký tài khoản tại 12BET khá đơn giản và dễ thực hiện. Chỉ cần bỏ ra vài phút là bạn đã có ngay một tài khoản mới tinh tại nhà cái này.
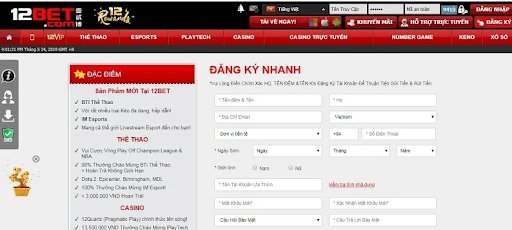
Đăng ký tài khoản
Qua hình bên trên mọi người có thể thấy thủ tục tại 12BET khá đơn giãn chỉ cần thực hiện những bước sau để hoàn thiện:
- Bước 1: Truy cập vào trang chủ của 12BET và chọn vào đăng ký ở góc phải bên trên màng hình
- Bước 2: Điền đầy đủ thông tin và nhấn đăng như như hình miêu tả bên trên
- Bước 3: Kiểm tra lại thông tin sau đó nhấn đăng ký và hoàn tất đăng ký
Đăng nhập tài khoản tại 12BET
Không khác gì mấy đối với thủ tục đăng ký. Đăng nhập vào 12BET cũng sẽ được thực hiện bởi những bước sau:
- Bước 1: Truy cập vào trang chủ 12BET.
- Bước 2: Chọn phần đăng nhập trên góc phải màng hình như hình miêu tả
- Bước 3: Điền thông tin và đăng nhập vào tài khoản
Nạp và rút tiền tại 12BET
Nhằm mang đến sự tiện ích tối đa cho khách hàng, 12BET đã không ngừng nâng cấp dịch vụ mỗi ngày để mang đến cho khách hàng những trải nghiệm tốt nhất.
Ngoài đầu tư về chất lượng game thì 12BET còn chú trọng đến những thủ tục nạp, rút tiền khiến khách hàng hài lòng tuyệt đối.
Nạp tiền
Việc nạp tiền khá đơn giãn vì ngày nay 12BET đã tạo ra nhiều cổng thanh toán để giúp người chơi có thể nạp một cách tiện lợi nhất có thể.
Quy trình nạp tiền nhanh chóng
Quy trình nạp tiền tại nhà cái 12BET bao gồm các bước như sau:
- Bước 1: Đăng nhập vào nhà cái 12BET bằng đường link chính thống và click chọn “Nạp tiền” ở góc phải màn hình.
- Bước 2: Lựa chọn hình thức nạp tiền phù hợp với nhu cầu.
- Bước 3: Điền đầy đủ thông tin nạp tiền.
- Bước 4: Sau khi kiểm tra thông tin nạp tiền đã chính xác thì bạn click chọn “Nạp tiền”.
- Bước 5: Hệ thống thông báo thành công tức là tiền đã có trong tài khoản game của bạn.
Các hình thức nạp tiền tại 12BET
Với nhiều cách nạp khác nhau tại 12BET mà người chơi có vẻ thấy khá tiện lợi như:
- Thanh toán thủ công
- Nạp tiền SIÊU NHANH cùng Smartpay
- Nạp tiền qua ví điện tử Momo
- Nạp tiền bằng thẻ cào điện thoại
Việc tạo ra nhiều cổng nạp tiền như vậy không phải là sự rườm rà mà 12BET tạo ra mà để mọi người có thể tiện lợi hơn cũng như khi bạn gặp một vấn đề nào không thể nạp được thì có thể lựa chọn cho mình cách nạp khác nhau để dễ dang hơn.
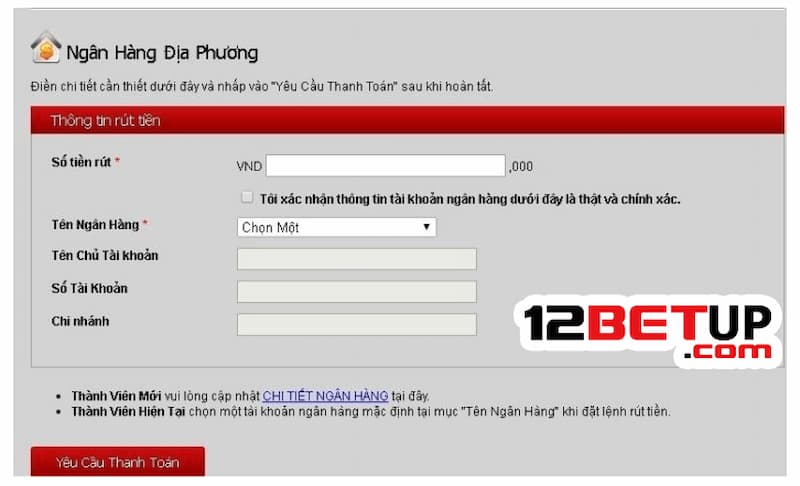
Rút tiền
Hiện tại quá trình rút tiền được 12BET sử dụng để bạn có thể rút được số tiền của mình thông qua nhiều hình thức khác nhau với nhiều ngân hàng khác nhau như vậy quá tiện lợi rồi đúng không.
Muốn rút tiền từ tài khoản game về tài khoản cá nhân bạn cần thực hiện theo hướng dẫn sau:
- Bước 1: Truy cập vào website 12BET và chọn mục “Rút tiền”.
- Bước 2: Lựa chọn hình thức nạp tiền phù hợp nhất.
- Bước 3: Điền đầy đủ thông tin nạp tiền mà hệ thống yêu cầu.
- Bước 4: Kiểm tra lại chính xác những thông tin đã điền sau đó nhấn “Xác nhận”. Chờ trong vài phút là tiền sẽ nằm gọn trong tài khoản cá nhân.
Đánh giá của người dùng về 12BET
Trong nhiều năm qua, 12BET được đông đảo anh em đánh giá là nhà cái uy tín, chất lượng hàng đầu thế giới.
Nhà cái này chăm chút tỉ mỉ trong từng dịch vụ, từ cách chăm sóc khách hàng đến những tựa game nhà cái cung cấp, hình thức nạp rút tiền, giao diện website,…
Nói chung mọi thứ từ phía nhà cái 12BET đều rất hoàn hảo và không có bất kỳ điều gì phải phàn nàn.
Giao diện dễ sử dụng
Tại nhà cái này không chỉ có đa dạng các tựa game mà tỷ lệ cược rất phong phú, đặc biệt thiết kế đồ họa bắt mắt và giao diện dễ sử dụng.
Chỉ cần truy cập vào đúng đường link trang chủ của website 12BET là bạn đã có thể tha hồ chơi game và cá cược dễ dàng.
Mọi thao tác, quy trình nạp hay rút tiền như thế nào đều được 12BET tối ưu hóa nên sẽ không khiến bạn mệt mỏi vì những thủ tục này, gây ảnh hưởng hay gián đoạn đến quá trình trải nghiệm game.
Ngoài ra, hệ thống game của 12BET còn vận hành khá mượt mà, nhanh chóng và lưu loát. Do đó, giúp người chơi có thể trải nghiệm nhiều tựa game mà không bị out.
Đầy đủ chức năng cần thiết
12BET thiết kế giao diện website rất khoa học, phân chia từng hạng mục, loại game cụ thể. Điều này giúp cho người chơi dễ dàng chọn được tựa theo đúng sở thích một cách nhanh chóng nhất.
Thêm vào đó, mỗi tựa game 12BET còn trang bị đầy đủ những chức năng cần thiết để người chơi có thể cá cược một cách thuận tiện nhất và tăng tỷ lệ thắng cược cao.
Các câu hỏi thường gặp
Việc chơi game đổi thưởng trực tuyến không chỉ để giải trí, giải tỏa căng thẳng, áp lực sau những ngày bận rộn với công việc mà còn giúp anh em kiếm được một khoảng tiền lớn để thực hiện những dự định hiện tại, tương lai.
Vì thế mà, trước khi bắt đầu chơi cá cược tại 12BET, hầu hết anh em luôn có vô vàn những thắc mắc liên quan đến nhà cái. Dưới đây là các câu hỏi mà nhiều người chơi quan tâm đến nhất.
Tôi không rút được tiền tại 12BET phải làm sao?
Trong trường hợp bạn không rút được tiền tại 12BET hãy kiểm tra lại thông tin rút tiền cung cấp đã chính xác chưa hoặc bạn có tham gia chương trình khuyến mãi nào của nhà cái không. Nếu thông tin rút tiền chưa chính xác hoặc bạn đang tham gia chương trình khuyến mãi nào nhưng chưa hoàn thành điều kiện thì sẽ không thể rút được tiền. Hoặc cũng có thể liên hệ với bộ phận CSKH của nhà cái 12BET để được hỗ trợ.
Tải và cài đặt app mobile 12BET có mất phí không?
Không. Bạn có thể tải và tải app 12BET mobile cho Android hoặc iOS. Cả 2 phiên bản ứng dụng của nhà cái hoàn toàn miễn phí.
Rút tiền tại 12BET có bị mất phí dịch vụ không?
Không. Hiện nay nhà cái 12BET đang hỗ trợ nhiều phương thức nạp rút tiền. Tuy nhiên, dù bạn lựa chọn phương thức nào, số tiền rút bao nhiêu cũng không bị mất phí dịch vụ.
Cá cược tại 12BET có hợp pháp không?
Để duy trì được một khoản thời gian khá lâu và phát triển nó là điều mà 12BET đã nói lên tất cả vì sao mà nhà cái này tồn tại đến bây giờ.
Vì 12BET là nhà đối tác lớn của Techplay, Ezugi, Vivogaming,… và dưới sự bảo trợ của nhiều đối tác lớn trong và ngoài nước…
Bên cạnh đó cũng có phần của nhiều anh em đã chơi tại 12BET. Đã tin tưởng và lựa chọn 12BET là nhà cái uy tín để kèo cược cho mình và hơn nữa đã tạo ra một sân chơi vô cùng lớn tại Việt Nam ở thời điểm hiện tại. Chính vì vậy mà bạn hãy yên tâm về độ tin cậy cũng như bảo mật của 12BET nhé.
Mọi quyền lợi của người chơi đều được PAGOR bảo hộ nên mức độ an toàn khi chơi game và tham gia cá cược tại 12BET là tuyệt đối.
Do đó, bạn không cần bận tâm bất cứ điều gì liên quan đến tiền thưởng, thông tin cá nhân… khi chơi game đổi thượng tại nhà cái 12BET.
Dịch vụ CSKH 12BET có tốt không?
Đây luôn là câu hỏi được mọi người chơi mới lẫn cao thủ cá cược cũ quan tâm đến. Bởi nhà cái có dịch vụ chăm sóc khách hàng chu đáo sẽ mang lại sự thuận tiện, an tâm hơn cho người chơi.
Cũng giống như nhiều nhà cái khác 12BET vẫn luôn tạo ra một môi trường ưu tiên và chú trọng đến khách hàng là người chơi của mình. Vì vậy việc CSKH đã trở nên một điều khá quan trọng đối với 12BET.
Qua hình bên trên nhà cái 12BET đã phần nào minh bạch được thông tin cũng như quy mô và việc CSKH của họ khá là chuyên nghiệp và đã tạo riêng cho khách hàng một nơi để có thể liên lạc và giải đáp nhiều câu hỏi khác nhau qua nhiều hình thức như:
- Số điện thoại: 036.39.77282
- Zalo: 036.39.77282
- Viber: 036.39.77282
- Email: cskh@12BET
Quá tiện đúng không nào tại đây 12BET sẽ giải đáp hầu hết những thắc mắc của mọi người khi tham gia kèo cược tài nhà cái 12BET.
Kết luận
Với nhiều năm kinh nghiệm tạo ra ra sân chơi cho anh em đam mê bộ môn kèo cược. Đề cao chất lượng cho người chơi tại Việt Nam với đa dạng sản phẩm và chất lượng dịch vụ hàng đầu thế giợi.
Không chỉ vậy đó điều mà khiến cho người chơi tin tưởng ở 12BET là sự bảo mật tuyệt đối cho người chơi là một ưu điểm nổi bật.
Người chơi có thể tin tưởng và chọn 12BET là sân chơi của mình là điều hiển nhiên rồi. Còn chần chừ gì nữa mà không đến ngay 12BET để nhận ngay ưu đãi và bắt đầu những kèo cược đầu tiên tại đây.